Complete UAF exploit - UD Capture
Por um escritor misterioso
Descrição
A Survey of Detection Methods for Software Use-After-Free
General David H. Petraeus, US Army (Ret.) on LinkedIn

Automated Use-After-Free Detection and Exploit Mitigation: How Far

Automated Use-After-Free Detection and Exploit Mitigation: How Far
The big heap adventure. Mastering heap exploitation techniques on

CVE-2018-8611 Exploiting Windows KTM Part 3/5 – Triggering the

Estimating the Bit Security of Pairing-Friendly Curves

Released! PS5 Kernel exploit + Webkit vulnerability for Firmware

Automated Use-After-Free Detection and Exploit Mitigation: How Far

Use-After-Use-After-Free Exploit UAF by Genrating Your Own

uaf' — CTF by pwnable.kr. So, for those of you who don't know

Exploiting a Use-After-Free (UAF) Vulnerability - Unsubscriptions
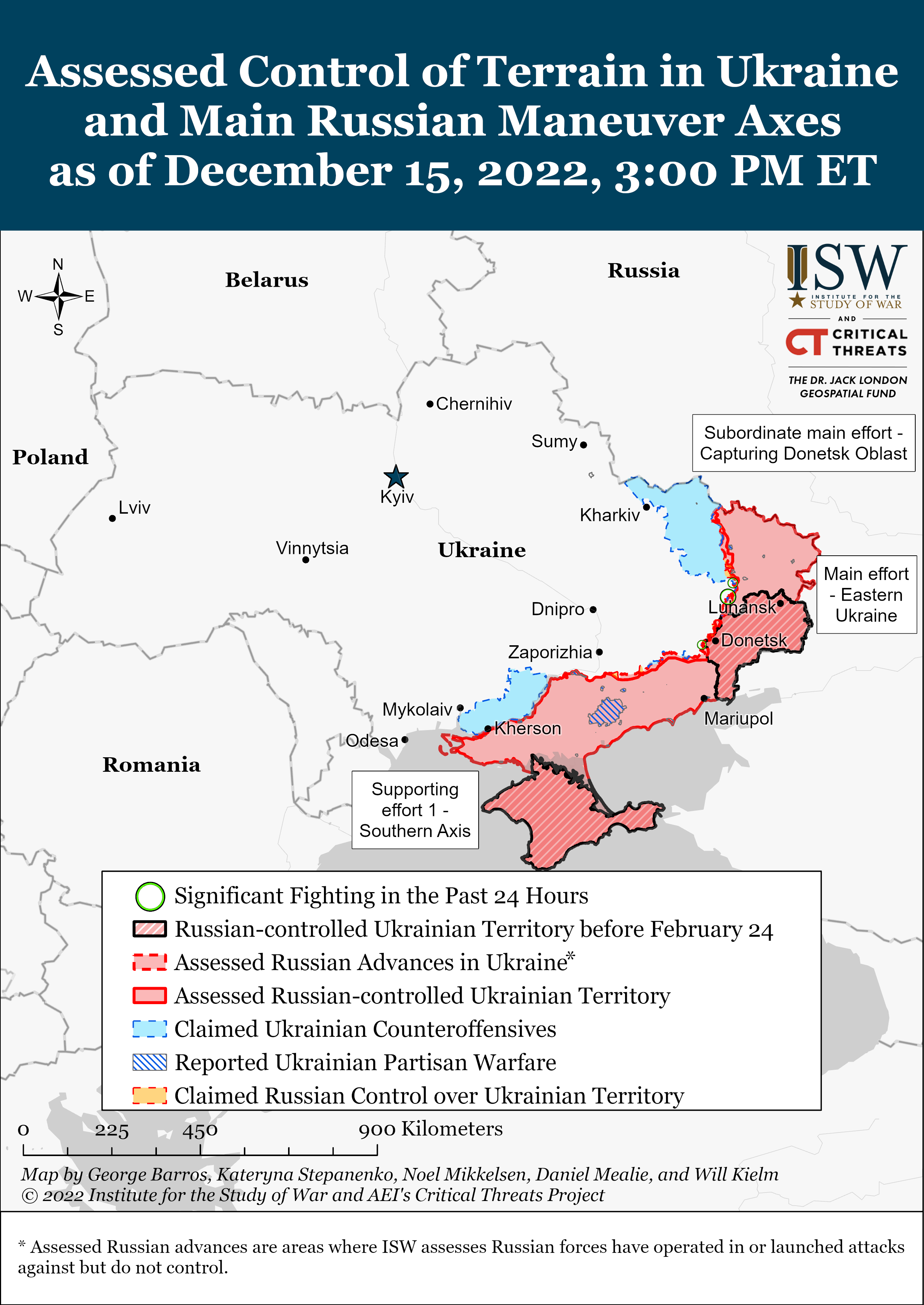
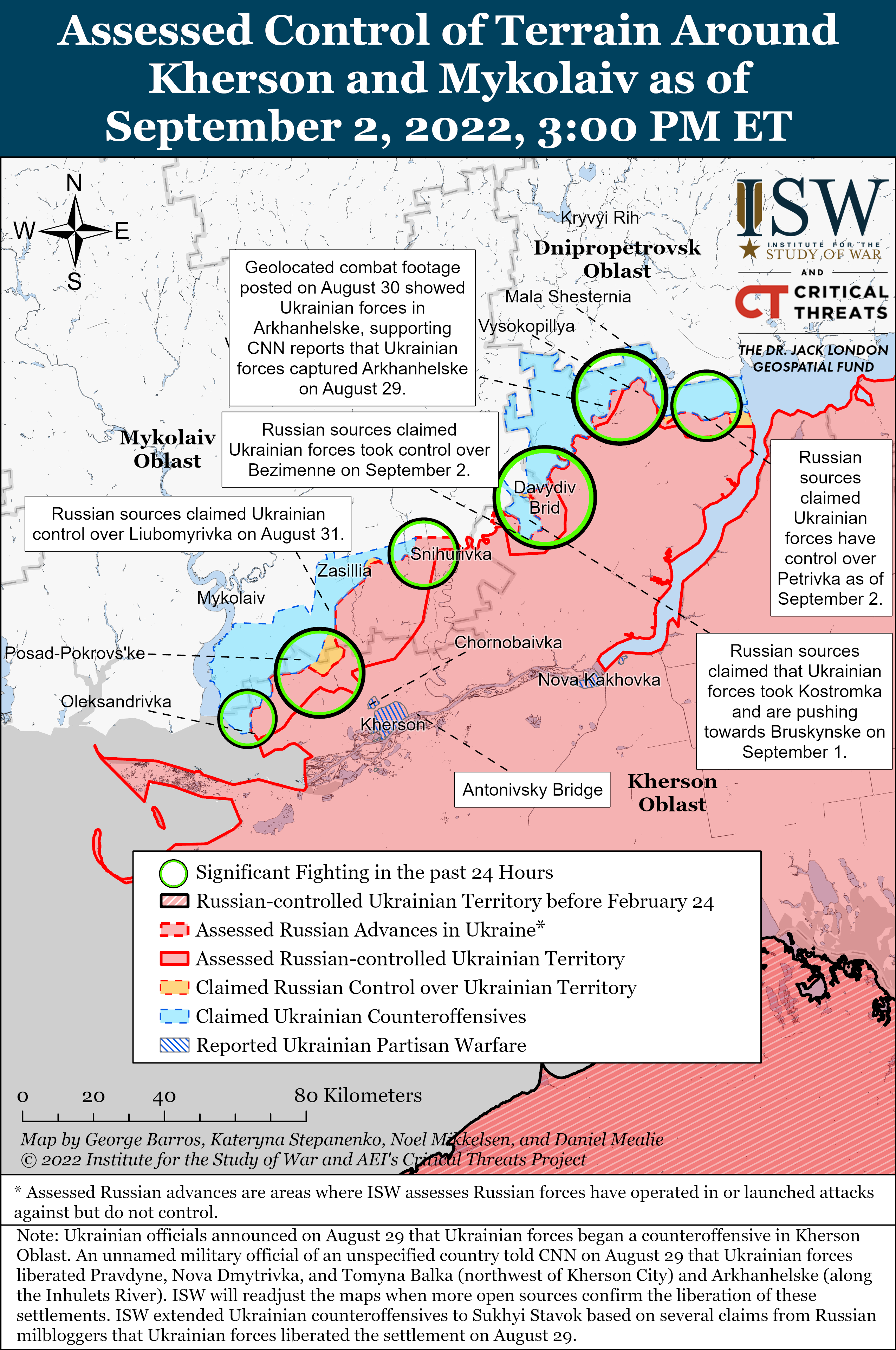
Ukraine Conflict Updates 2022 Institute for the Study of War
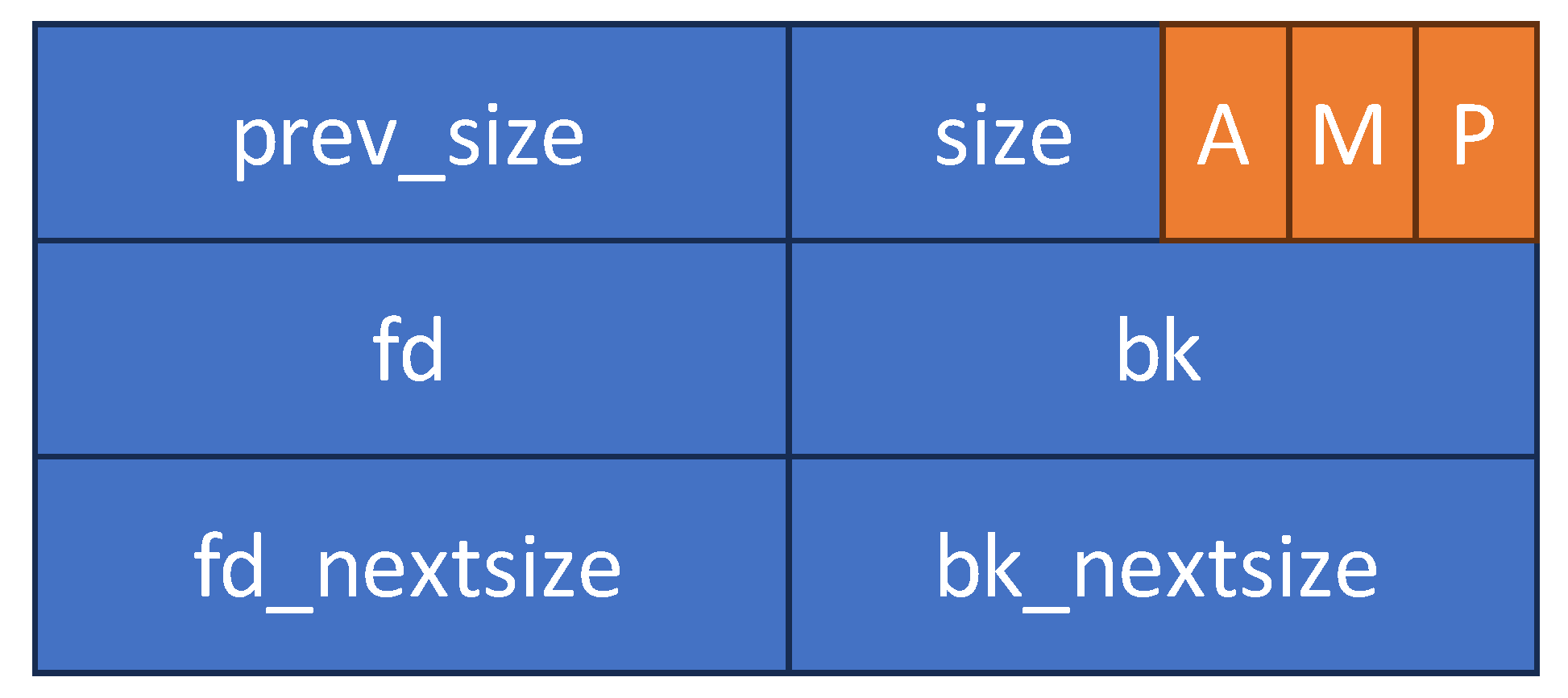
Symmetry, Free Full-Text

Use-After-Use-After-Free: Exploit UAF by Generating Your Own
de
por adulto (o preço varia de acordo com o tamanho do grupo)






/i.s3.glbimg.com/v1/AUTH_5dfbcf92c1a84b20a5da5024d398ff2f/internal_photos/bs/2023/C/t/Qd2I03QvWsIjGaQVlH8Q/whatsapp-image-2023-02-07-at-07.22.28.jpeg)