Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Detail procedure of malware analysis

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog

Interactive Online Malware Sandbox

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus

Cybersecurity Search Engine

Malware Analysis: Steps & Examples - CrowdStrike

Malware analysis file Malicious activity

A detailed analysis of the Menorah malware used by APT34

StopRansomware: Rhysida Ransomware

TryHackMe Hacktivities
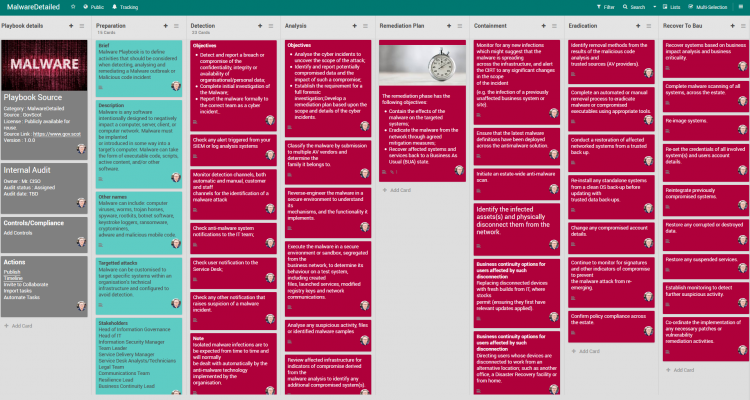
Playbook for Malware outbreak

Endpoint Detection and Response, Free - What is EDR Security?
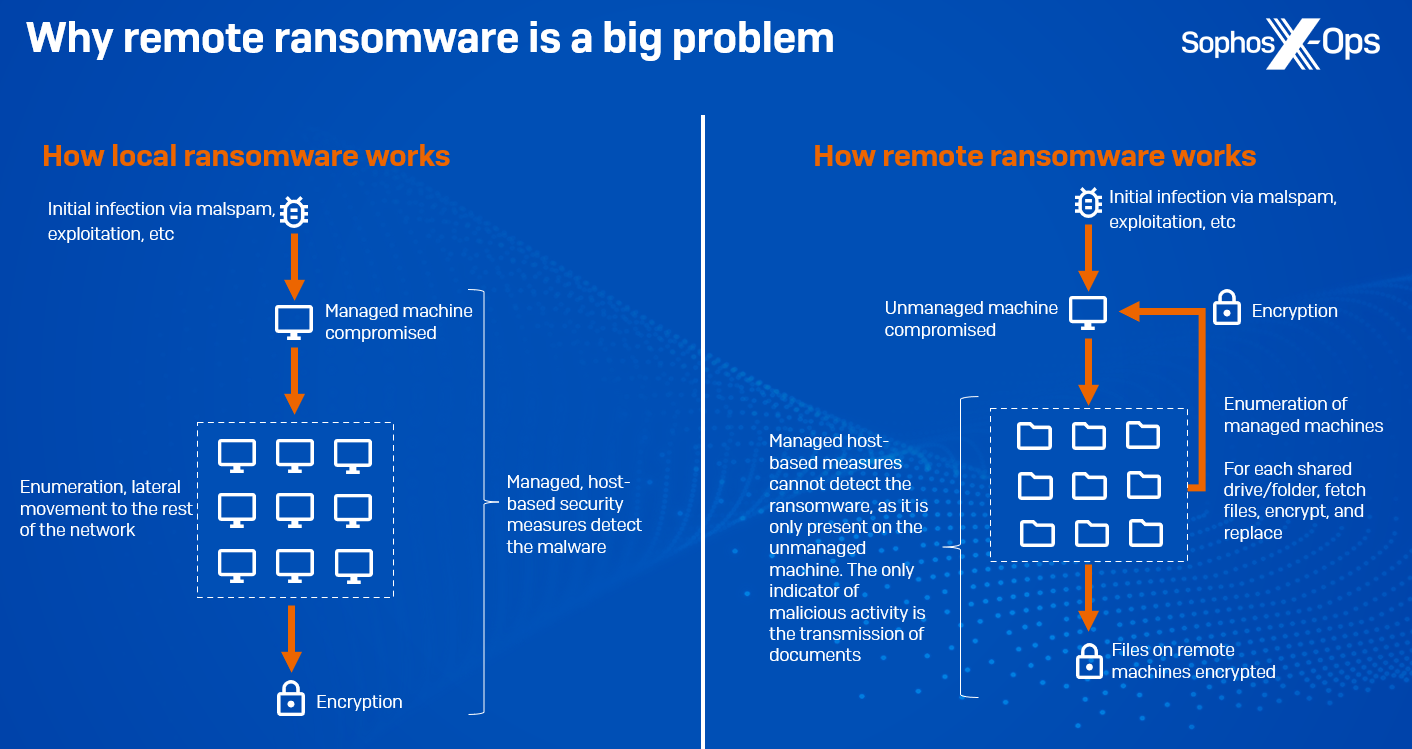
CryptoGuard: An asymmetric approach to the ransomware battle – Sophos News
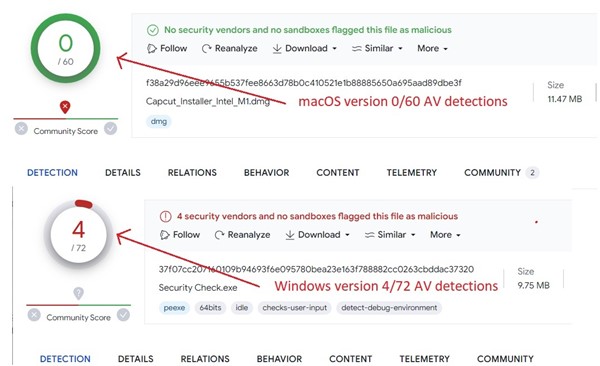
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows
de
por adulto (o preço varia de acordo com o tamanho do grupo)