Towards an Automated Process to Categorise Tor's Hidden Services
Por um escritor misterioso
Descrição

TOR Fronting — Utilising Hidden Services to Hide Attack Infrastructure, by Vincent Yiu

Design and Synthesis of Novel Oxime Ester Photoinitiators Augmented by Automated Machine Learning
Egregor ransomware: Maze's heir apparent – Sophos News
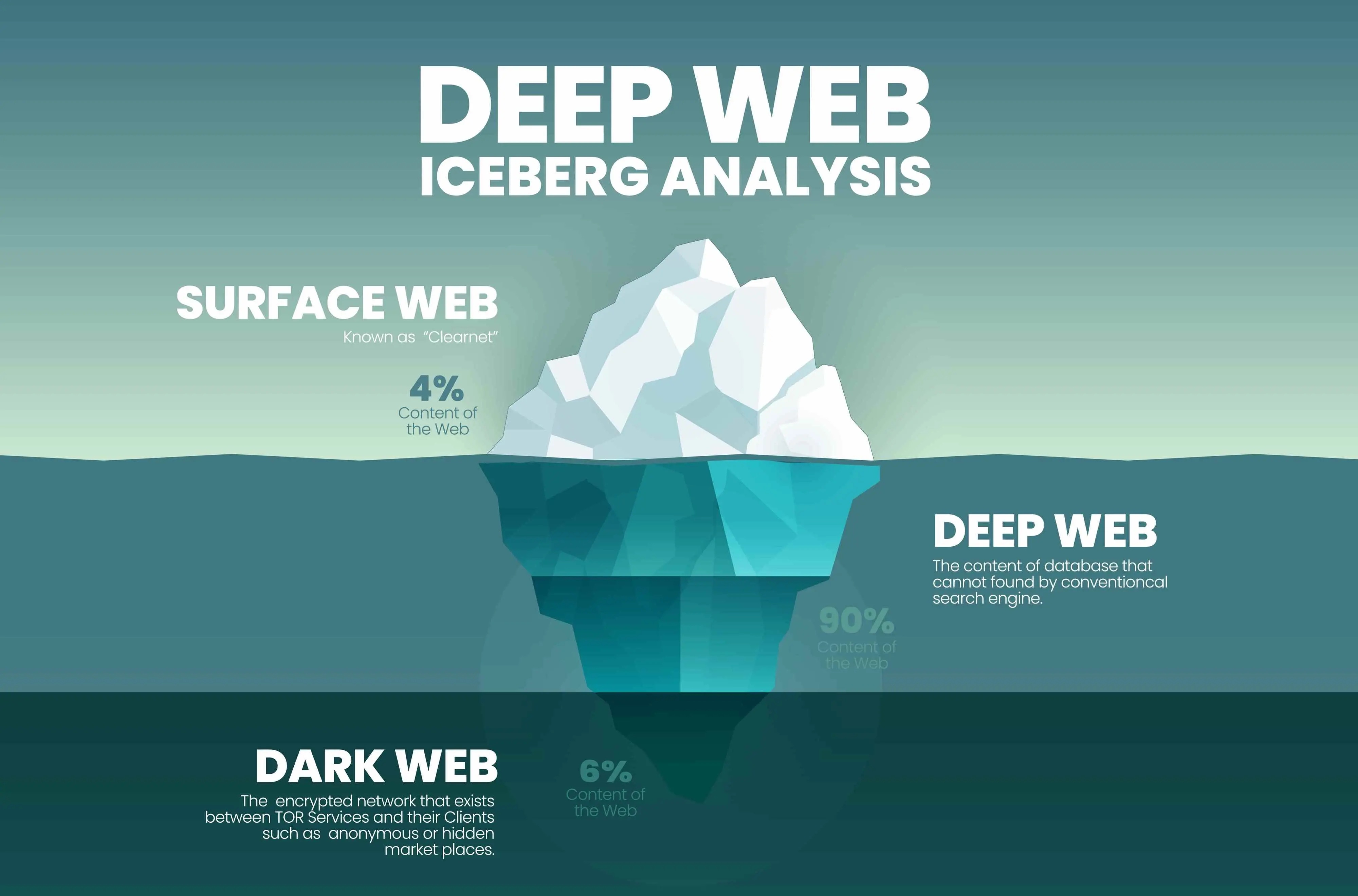
The Deep Web & The Dark Web

Operation Excellence: How LINSTOR is Redefining Military Data Storage - LINBIT

TOR Fronting — Utilising Hidden Services to Hide Attack Infrastructure, by Vincent Yiu

How to buy breached data on the dark-web.fast! - Polymer
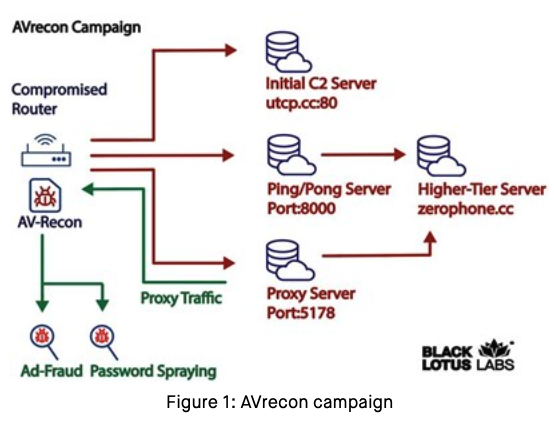
Who and What is Behind the Malware Proxy Service SocksEscort? – Krebs on Security

Journal of Automation, Mobile Robotics and Intelligent Systems, vol. 16, no. 4 (2022) by Ł-PIAP - Issuu

14 Things to Check When a System Gets Compromised - The Sec Master
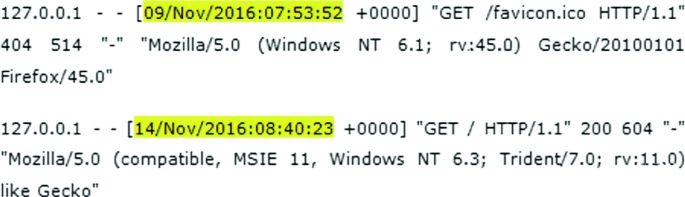
Towards an Automated Process to Categorise Tor's Hidden Services

The Art of Invisibility: The World's Most by Mitnick, Kevin
10 Best Dark / Deep Web Browsers for Anonymity - SOCRadar® Cyber Intelligence Inc.
de
por adulto (o preço varia de acordo com o tamanho do grupo)