Trend Micro Research on X: Scenario 2: If the user is not logged
Por um escritor misterioso
Descrição
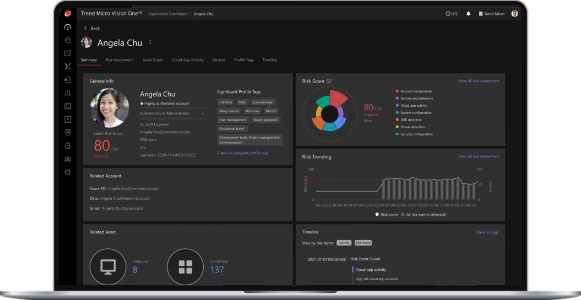
1 in Cloud Security & Endpoint Cybersecurity
Empty list for endpoint and domain nodes after agent deployment - OfficeScan
Collecting debug logs - Portable Security 3.0

Organisational use of Enterprise Connected Devices
Known issues - Licensing Management Platform
Collecting debug logs - Portable Security 3.0
Collecting debug logs - Portable Security 3.0
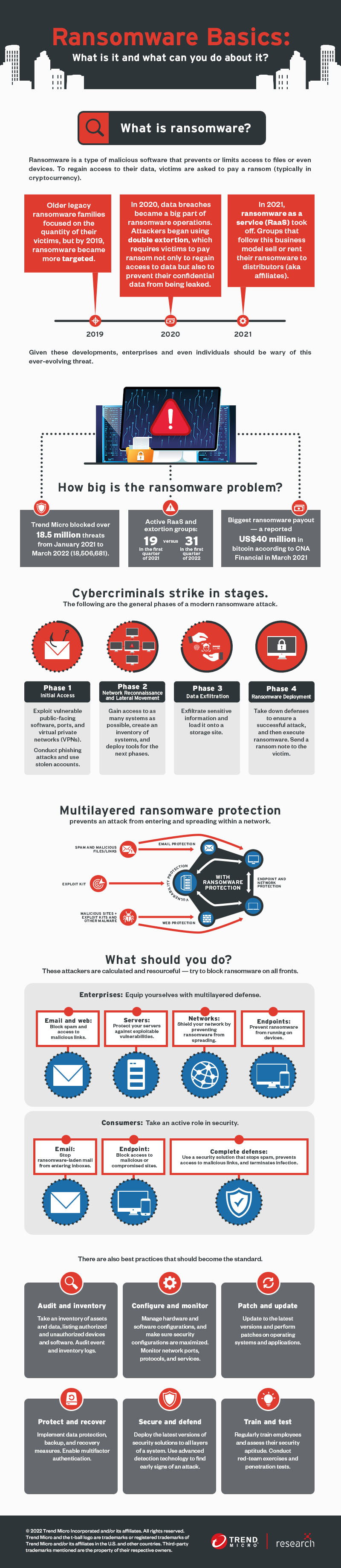
Ransomware - Definition

Clean Water through Nanotechnology: Needs, Gaps, and Fulfillment

Confusion Matrix: How To Use It & Interpret Results [Examples]
How to report misrated websites to Trend Micro

The Myth of Air Purifier in Mitigating the Transmission Risk of SARS-CoV-2 Virus - Aerosol and Air Quality Research
How to report misrated websites to Trend Micro

Climate change - Wikipedia
de
por adulto (o preço varia de acordo com o tamanho do grupo)

/cdn.vox-cdn.com/uploads/chorus_image/image/69547484/jbareham_190410_ply0870_0144_moltres.0.jpg)


