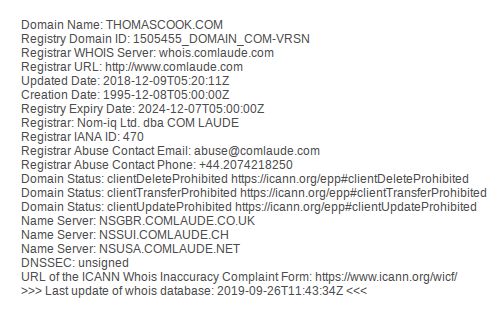
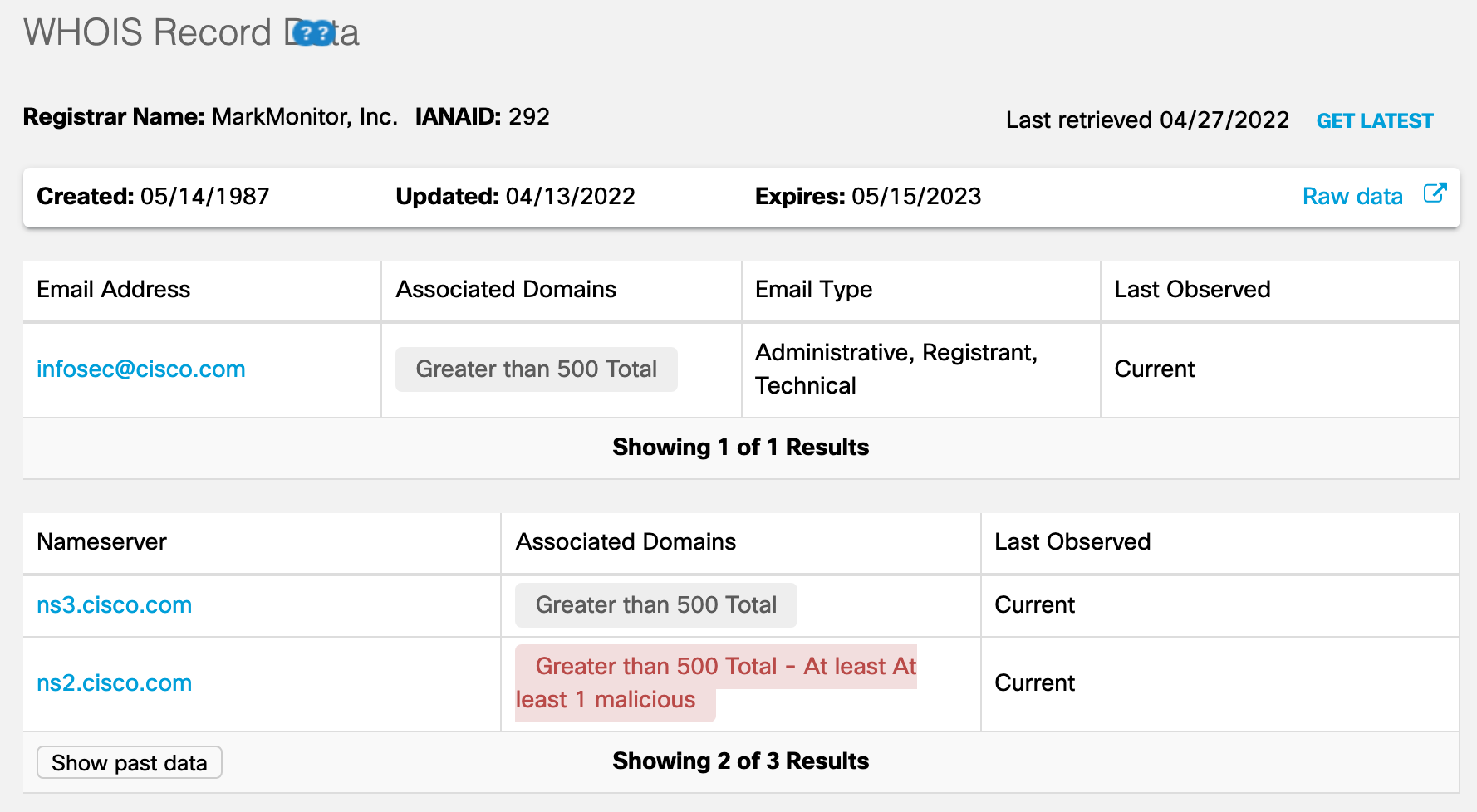
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Descrição
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

Should you use Let's Encrypt for internal hostnames? – Terence Eden's Blog

Infrastructure Hacking: Telnet Protocol » Hacking Lethani
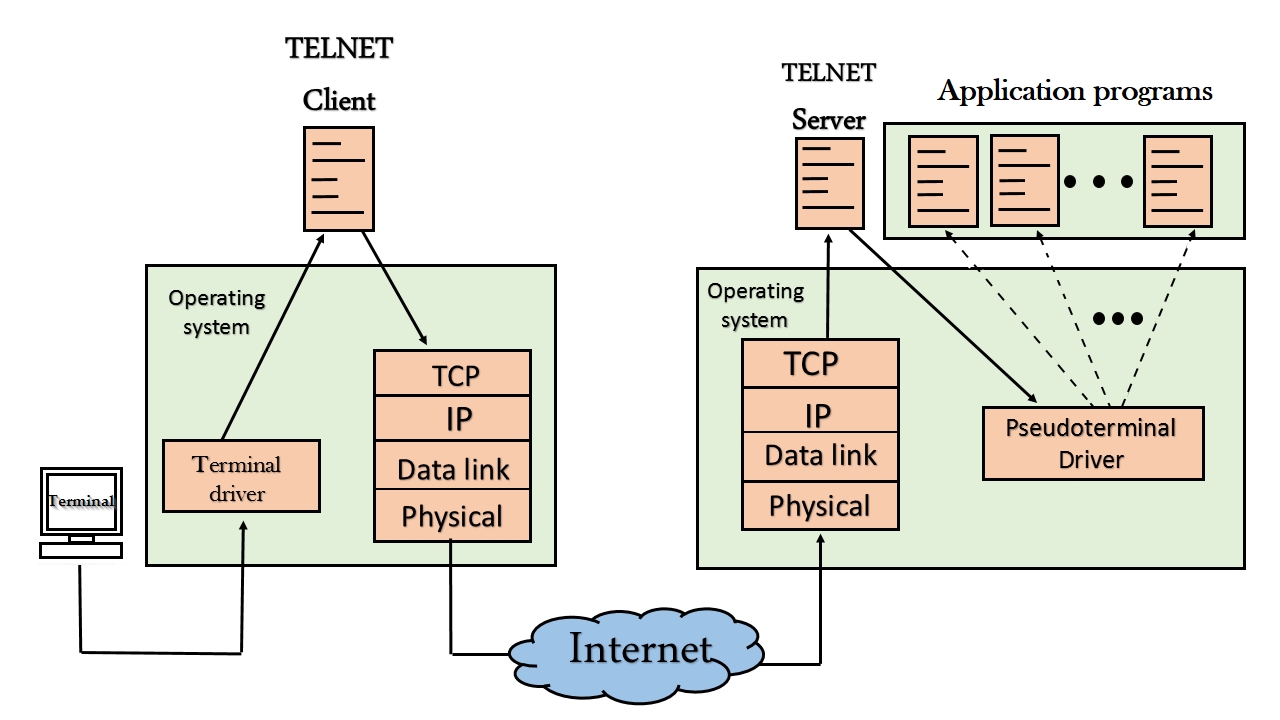
Infrastructure Hacking: Telnet Protocol » Hacking Lethani

Learn ethical hacking (@learn_hacking4) • Instagram photos and videos
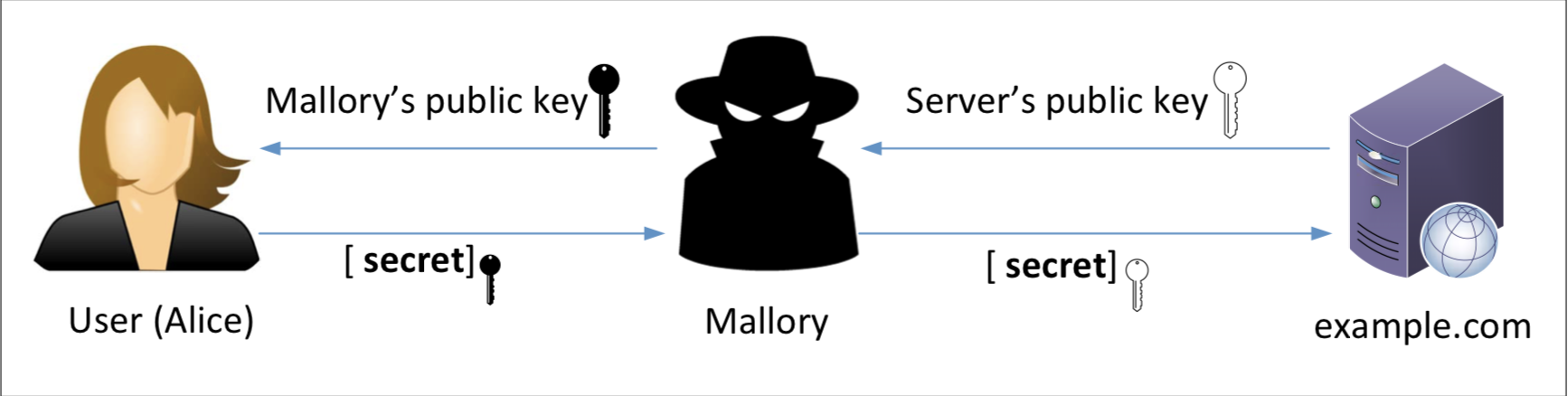
Network Security: Public Key Infrastructure Lab

Infrastructure Hacking: DNS Protocol II » Hacking Lethani

Infrastructure Hacking: DNS Protocol II » Hacking Lethani

N. Korean Hackers Distribute Trojanized CyberLink Software in Supply Chain Attack
Hack This Site: Realistic Web Mission — Level 13
de
por adulto (o preço varia de acordo com o tamanho do grupo)