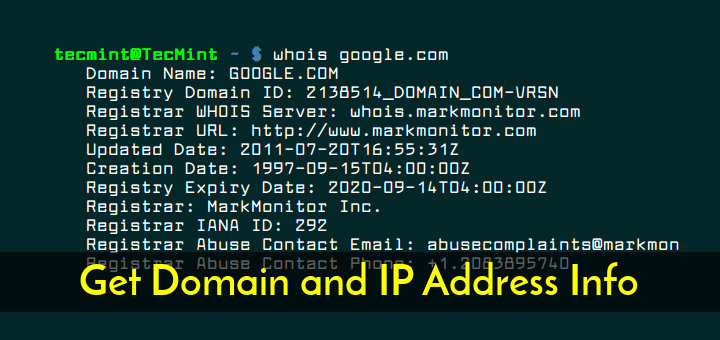
Screenshot of WHOIS query for IP address 185.158.248.XXX.
Por um escritor misterioso
Descrição

Accuracy, FPR, precision and recall values for intent data of the

Top 10 SAT with the highest frequency variation between malware and
Gambar 1. Diagram alir dari proses training. Proses training

Images of 3 filters randomly selected from the first convolutional layer

Commonly employed malicious software detection and analysis methods in

PDF) The Spy Next Door: A Digital Computer Analysis Approach for Backdoor Trojan Attack

Accuracy, FPR, precision and recall values for intent data of the

Categorias mais perigosas de Web Sites, de acordo com a Symantec

Ilker KARA, Asst. Professor Dr., Çankırı Karatekin Üniversitesi

Diagrama da Metodologia Proposta.

Obtained results of the first simulation scenario (nbn = 500, nbt = 2

GUI of the signature-based detection engine showing the scan results

Visualization of Malware Features in CoarseGrained Evaluation
de
por adulto (o preço varia de acordo com o tamanho do grupo)