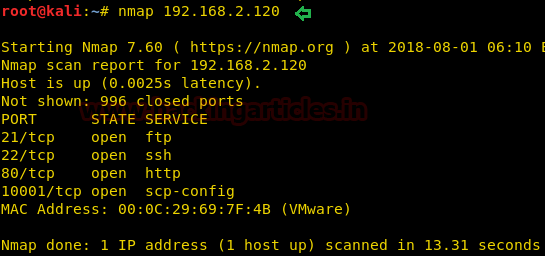
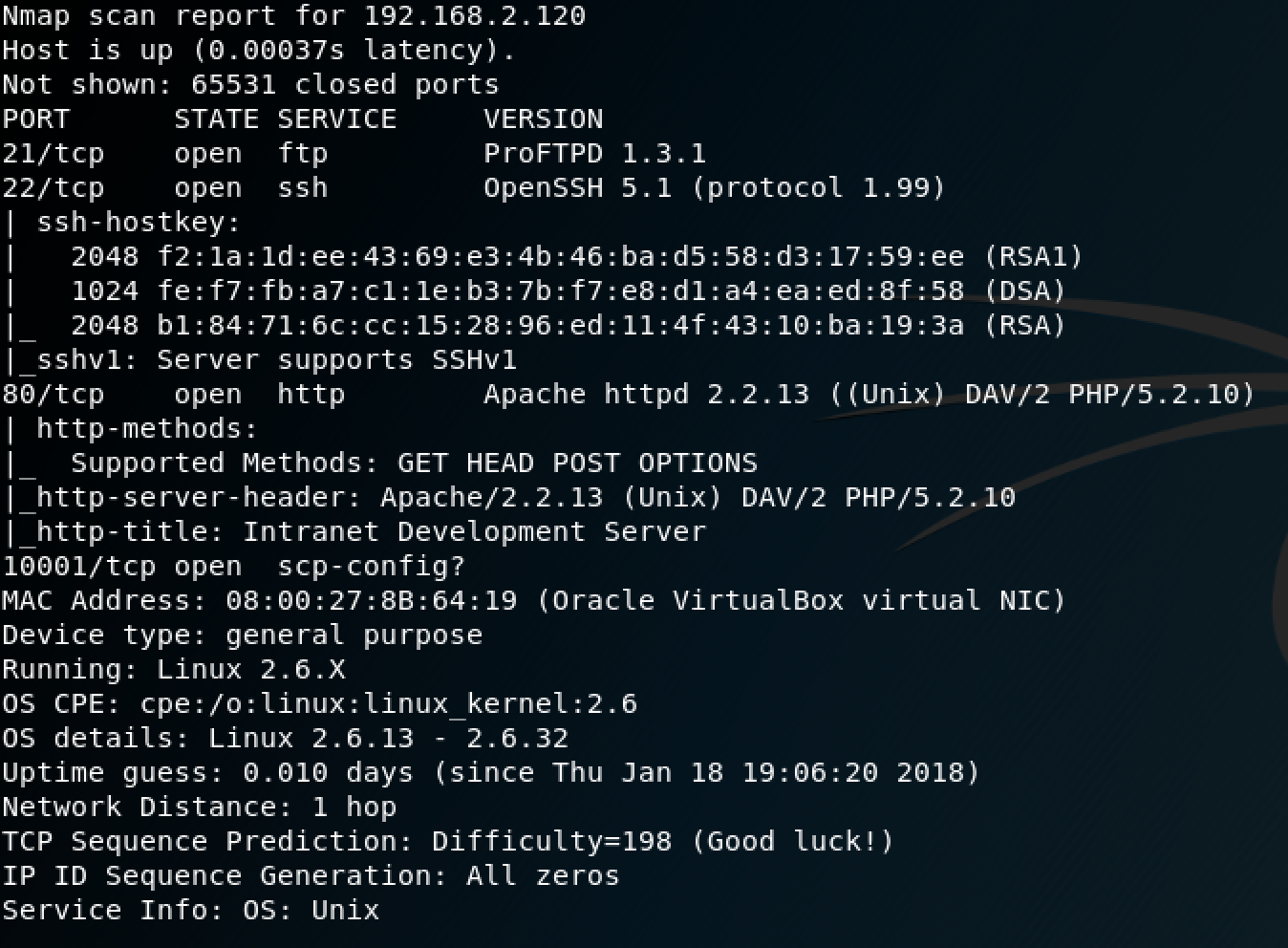
Kung fu enumeration. Data collection in attacked systems – HackMag
Por um escritor misterioso
Descrição
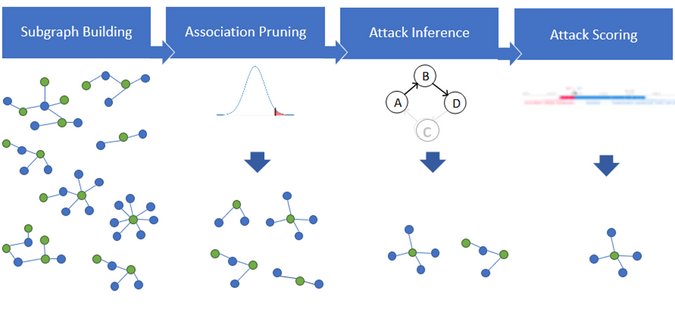
Behind the Scenes: The ML Approach for Detecting Advanced

Data Injection Attack - an overview
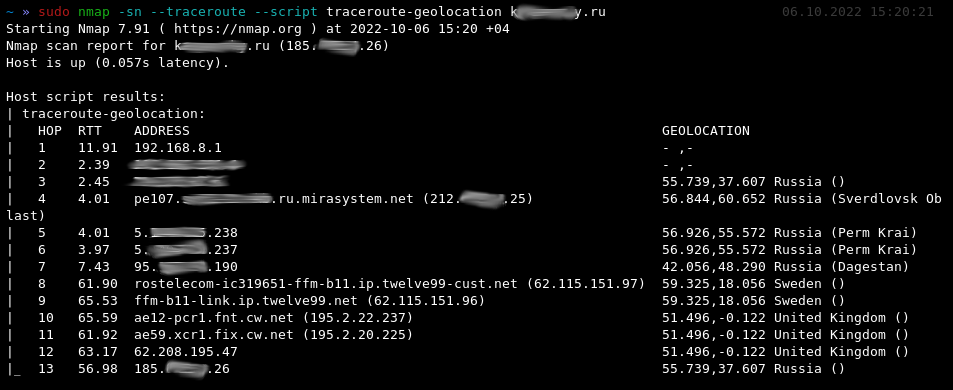
Kung fu enumeration. Data collection in attacked systems – HackMag
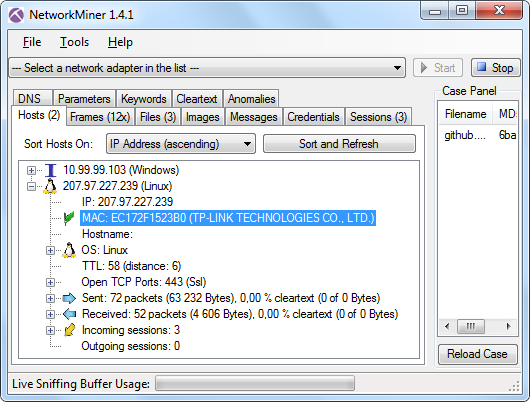
Forensics of Chinese MITM on GitHub

PHISHING FUNDEMANTALS. Imagine This, by Ibrahim Akdağ, Ph.D.

Counter Hack Reloaded: A Step-by-Step Guide to Computer Attacks
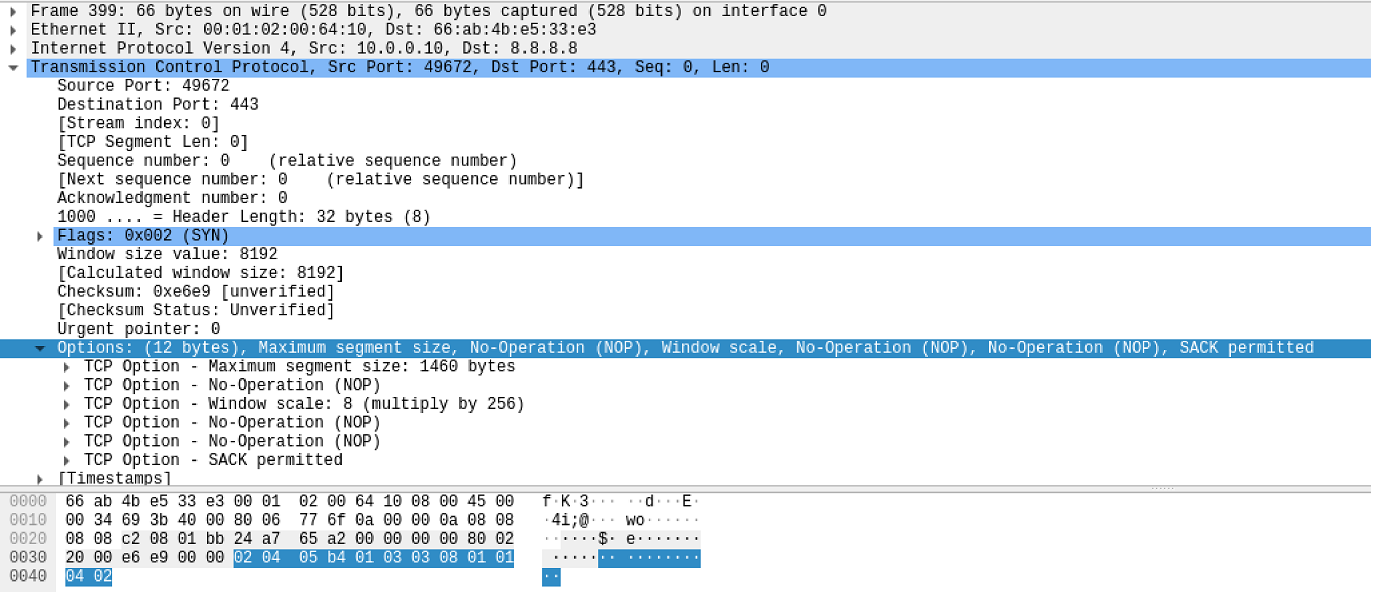
Kung fu enumeration. Data collection in attacked systems – HackMag

Interview with one of the world's best competitive bug hunters

Xiangyu Qi - CatalyzeX
de
por adulto (o preço varia de acordo com o tamanho do grupo)